Security operations
for modern infrastructure
Unified visibility across logs, network traffic, and endpoints. Built for correlation, investigation, and operational control.

Security risk continues to evolve
Breaches are more frequent, more costly, and harder to detect.

$4.4M — the global average cost of a data breach in 2025.

34% increase in attackers exploiting vulnerabilities to gain initial access and cause security breaches compared to last year's report.

Nearly 60% of small businesses hit by a cyber attack fail within six months—while global cybercrime losses are estimated at $1.2–1.5 trillion annually.

Around 4,000 cyber attacks happen daily—approximately one every three seconds—with 90% of all incidents starting from a phishing email.
Is Your Security Stack Giving You the Full Picture?
Centralize logs, network traffic, and endpoint telemetry into one platform to detect every threat.
How BluScout works
Designed for reliable operations, clear investigations, and flexible deployment.
Collect
Collect telemetry across endpoints, network, and log sources using deployment options that fit your environment.
- Multiple collection paths
- Secure transport
- Centralized onboarding
Normalize and correlate
Normalize data and correlate related activity across sources to build consistent context for investigations.
- Extensible parsing
- Correlation workflows
- Live updates
Detect & Respond
Prioritize higher confidence detections and support investigation and response workflows with clear, actionable context.
- Alerting and enrichment
- Investigation workflows
- Reporting support
Flexible deployment
Cloud-hosted in your VPC or deployed on‑premise. Align deployment with your governance and operational requirements.
Cloud-Hosted
We manage the infrastructure while you get a dedicated, isolated environment. Reduced operational overhead with strong isolation, security, and reliability.
On-Premise
Deploy on your own infrastructure for maximum control. Suitable for air‑gapped environments, strict compliance requirements, or when data must remain within your network.
Need help selecting a deployment model?
Designed for real security operations
One Platform,
One Experience
Reduce tool switching during investigations. BluScout brings key telemetry into a single workflow so teams can align on context and respond faster.
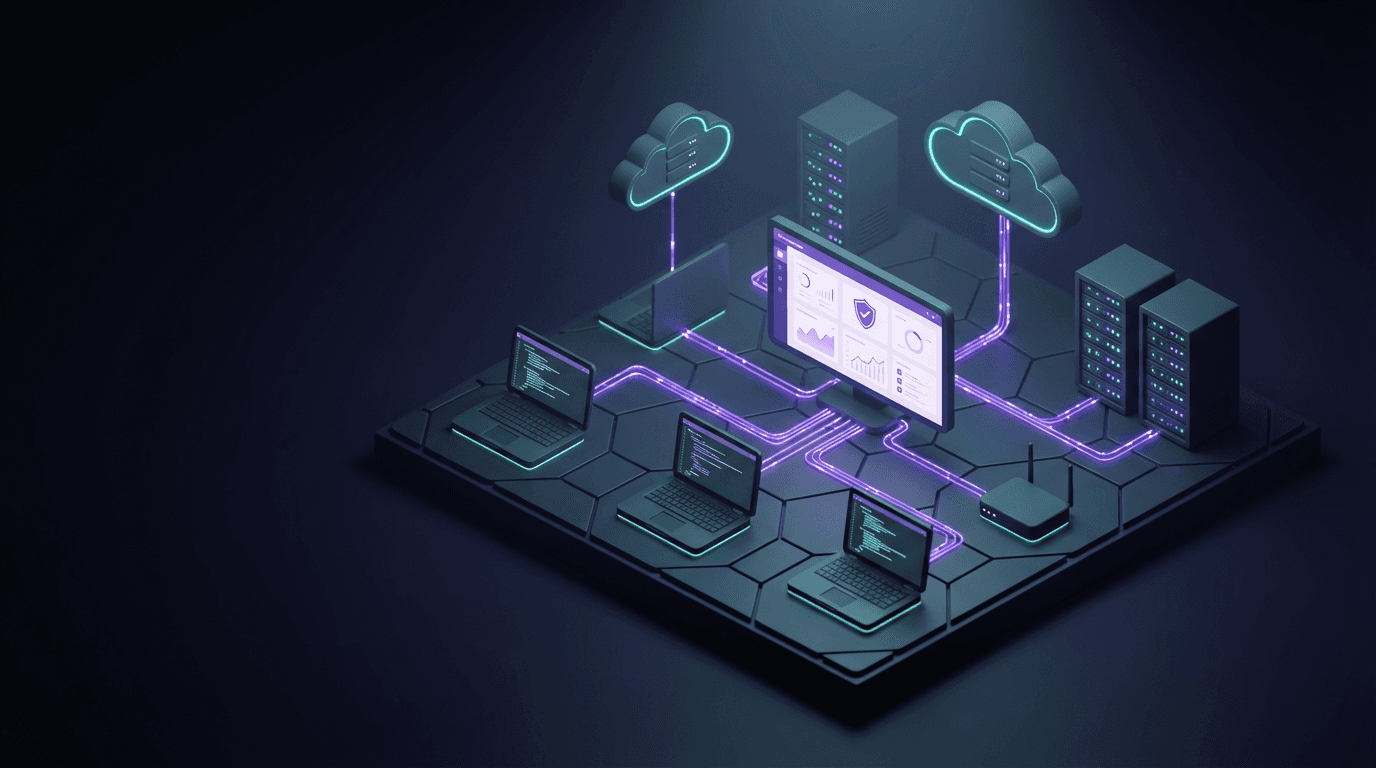
Inspect Every Layer
Add deeper network context when it matters. Use packet-level visibility to support investigations alongside logs and endpoint activity.
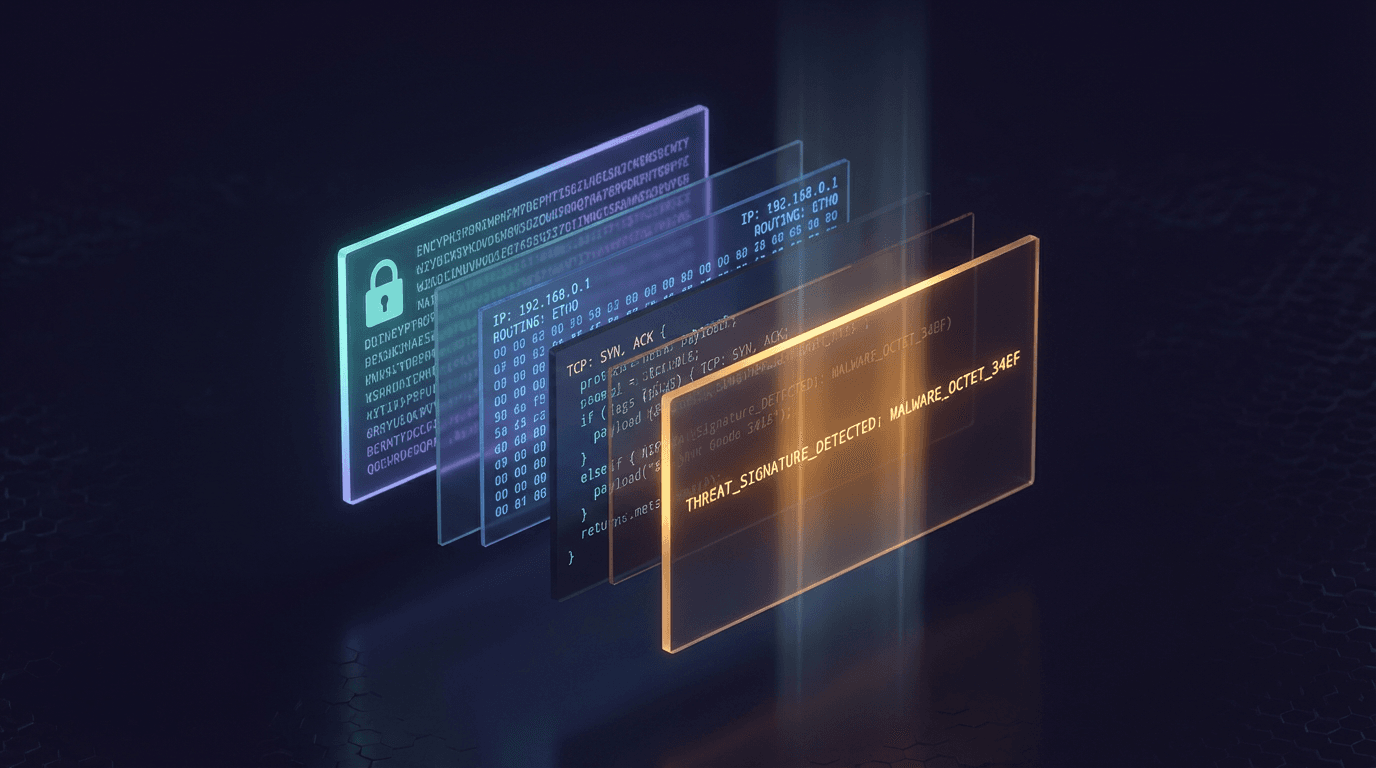
Cut Noise,
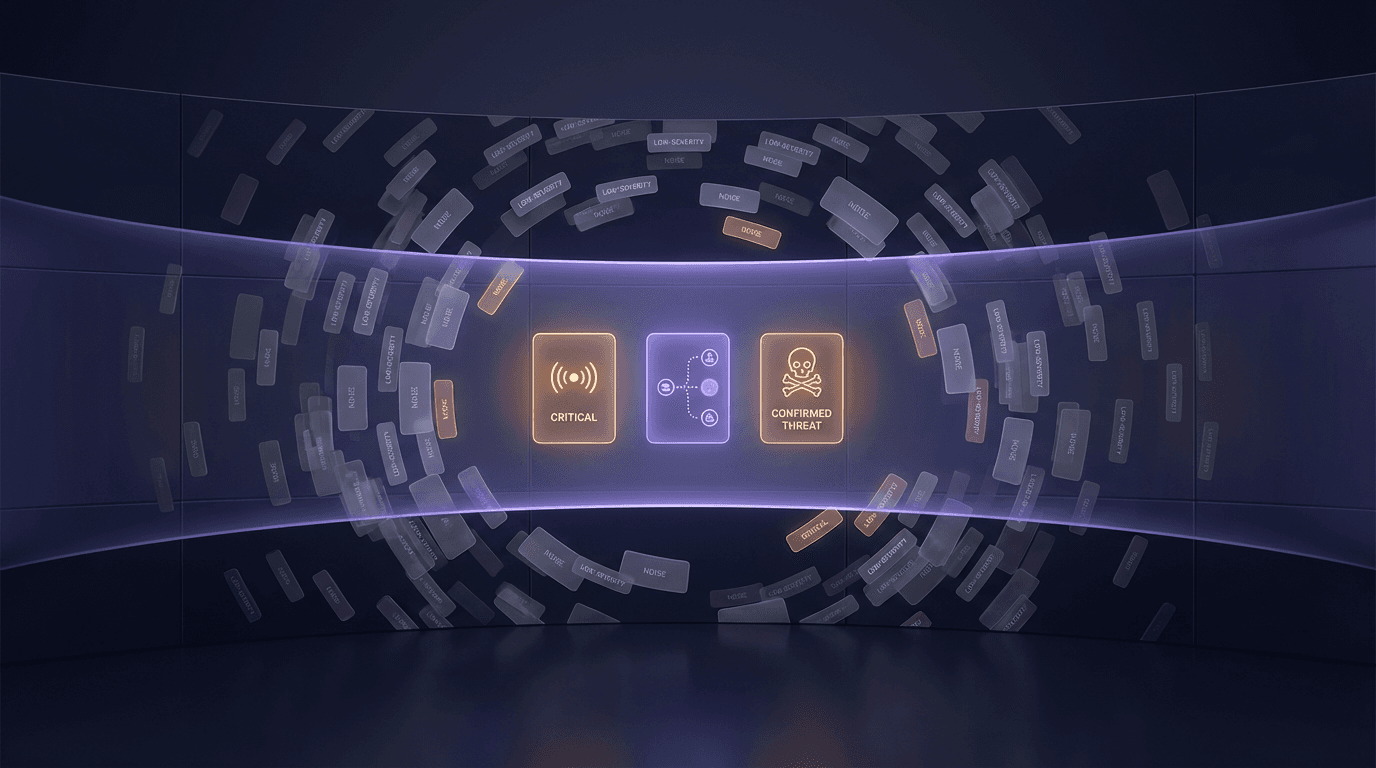
Keep What Matters
Improve signal quality with correlation-driven detections and flexible alerting. Prioritize higher confidence activity and keep investigations focused.
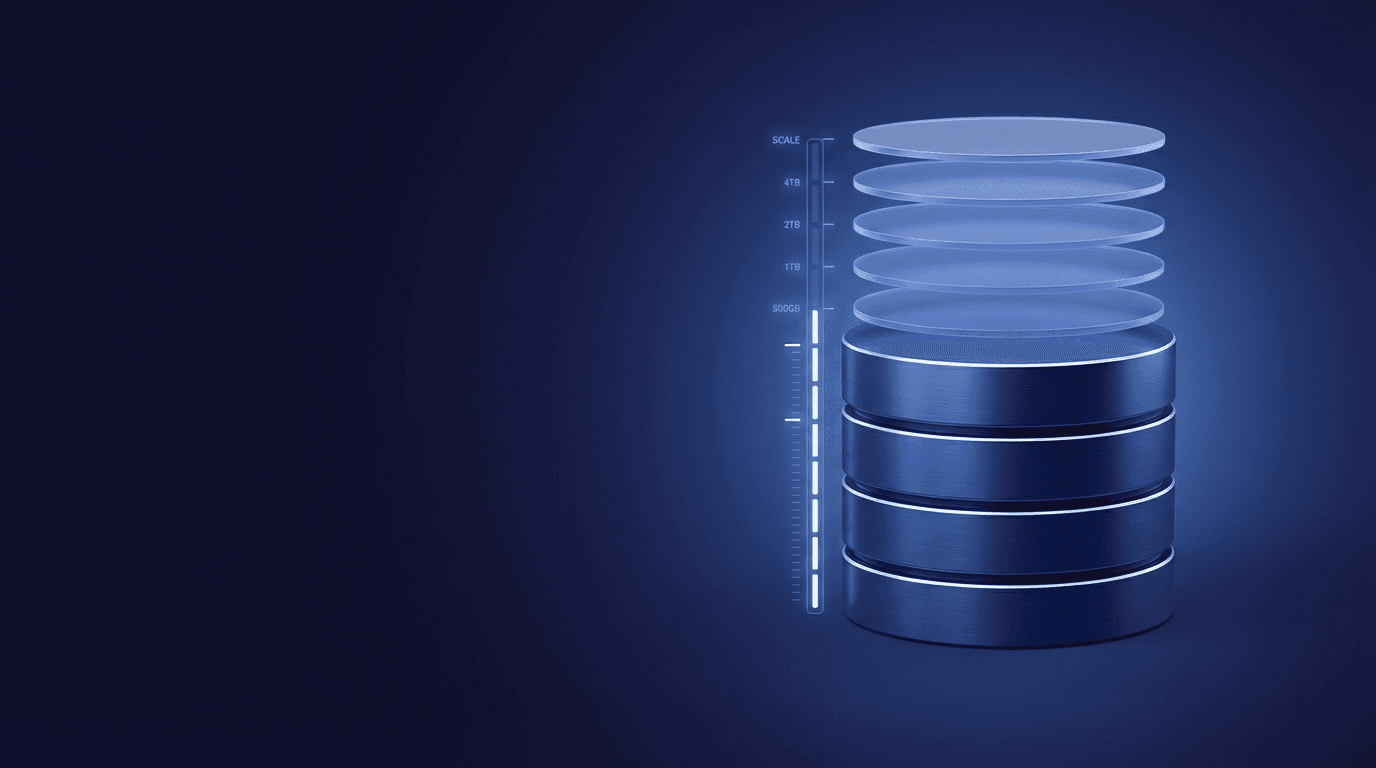
Retention and
capacity control
Plan retention and capacity with clear controls and governance workflows. Reduce surprises and align storage to policy and operational needs.
Frequently Asked Questions
Real answers for SOC teams evaluating modern security platforms
BluScout is designed to support enterprise scale ingestion and search. Performance and capacity depend on your deployment model, retention requirements, and data sources. During evaluation, we validate ingestion, retention, and search workflows against your environment.
Yes. BluScout supports investigations across logs, network activity, and endpoints. Teams can pivot between log and packet views using shared context (time ranges, entities, and related events) to accelerate triage and root cause analysis.
Deployment timelines vary by environment, telemetry sources, and governance requirements. We typically start with a scoped rollout, validate data collection and access controls, and then expand coverage based on operational needs.
Yes. You can create and maintain custom detections and parsing logic to match your environment. Updates are designed to be applied without operational disruption.
BluScout supports RBAC, audit trails, and retention controls to help organizations align security operations with internal policy and compliance programs. Deployment options include cloud, on‑premise, and hybrid models to support data residency requirements.
Pricing is based on deployment model, data volume, and retention requirements. See our pricing page for an overview, or contact us for a scoped quote based on your environment.
Your data remains accessible and exportable. We support practical data access and portability workflows so you can meet internal policy and long-term governance needs.
Yes. We can run a proof-of-concept in your environment to validate data sources, workflows, and deployment constraints before a broader rollout.